E-Commerce Notes
Unit-2
Lecture-1
Security Issues in E-Commerce Transactions
Ø
Authentication:- Authentication
ensures that the origin of an electronic message is correctly identified. This
means having the capability to determine who sent the message and from where or
which machine. Without proper authentication, it will be impossible to know who
actually placed an order and whether the order placed is genuine or not.
Ø Non-Repudiation:- Non-Repudiation is closely related to
authentication and this ensures that the sender cannot deny sending a
particular message and the receiver cannot deny receiving a message.
Ø Access Control:- If access control is properly implemented, many other
security problems like lack of privacy will either be eliminated or mitigated. Access
control ensures only those that legitimately require accesses to resources are
given access and those without valid access cannot have access.
Ø Confidentiality or Privacy:- Privacy ensures that only authorized
parties can access information in any system. The information should not be
distributed to parties that should not receive it. Issues related to privacy
can be considered as a subset of issues related to access control.
Ø
Integrity:- Integrity ensures that only
authorized parties can make changes to the documents transmitted over the
network.
Secure Electronic Transaction (SET)
v
Secure
Electronic Transaction (SET) is an open protocol which has the potential to
emerge as a dominant force in the security of electronic transactions.
v Jointly developed by Visa and
MasterCard, in conjunction with leading computer vendors such as IBM,
Microsoft, Netscape RSA, and GTE.
v
SET
is an open standard protocol for protecting the privacy and ensuring the authenticity
of electronic transactions.
§ Provide confidentiality of payment
and ordering information.
§ Ensure the integrity of all
transmitted data.
§ Provide authentication that a card
holder is a legitimate user of a credit card account.
§ Provide authentication that a
merchant can accept credit card transactions through its relationship with a
financial institution.
§ Ensure the use of best security
practices and system design techniques to protect all legitimate parties in an
electronic commerce transaction.
§ Create a protocol that neither
depends on transport security mechanisms nor prevents their use.
§ Facilitate and encourage
interoperability among software & network providers.
Participants in the SET system
Scope of SET
1.
Motivated
by the large amount of unsecured credit-card based transactions on the
Internet.
2.
Network
payments treated in a similar way to Mail Order/Telephone Order (MOTO)
transactions.
3.
SET
applies only to the ‘front end’ of payment no need to change the ‘back end’.
4.
SET
only addresses Payment - other protocols for shopping, payment method selection
etc. will be developed by others.
Secure Socket Layer (SSL)
v SSL is a protocol developed by
Netscape for transmitting private documents via the Internet.
v SSL uses cryptographic system that
uses two keys to encrypt data a public key known to everyone and a private or
secret key known only to the recipient of the message.
v The SSL provides end-to-end secure
data transmission between the web server and the web client.
v It is sandwiched between the TCP/IP
and the application layer.
v
Unlike
TCP/IP that offers only reliable packet transfer, SSL ensures secure packet
transfer.
How SSL works?
The SSL performs two functions-it
authenticates the websites and ensures secure data transmission between the web
server and the client.
It achieves this either by using
symmetric encryption or asymmetric encryption.
In symmetric encryption, a key called the private key is used
both for encrypting and decrypting the data. For symmetric encryption to work, the
sender & receiver should share the private key. This is possible only when
the sender & receiver know each other.
In asymmetric encryption, two separate keys are used to encrypt
& decrypt data. The public key is shared with the other person and the private
key is known only to the person who decrypts the data. So, the private key will
remain a secret while the public key will be known to both the parties.
E-Commerce Notes
Unit-2
Lecture-2
Cryptography
Cryptography is the process through
which the messages are altered so that their meaning is hidden from adversaries
who might intercept them.
Plain text is a message readable by anyone. Cipher text is plain text that has been modified to protect
its secrecy.
Encryption converts plain text to cipher text; Decryption converts cipher text to plain text.
“Cryptography
addresses the principles, means and methods used to disguise information in
order to ensure its authenticity”.
Cryptography is used to achieve:-
·
Confidentiality:
only authorized persons can access information.
·
Integrity:
information that was sent is what was received.
·
Authentication:
guarantee of originator of electronic transmission.
·
Non-repudiation:
originator of information cannot deny content or transmission.
Types of Cryptography:-
Ø Private Key Cryptography
Ø Public Key Cryptography
Private Key Cryptography
In private-key cryptography, the
sender and receiver agree beforehand on a secret private key. The plain text is
somewhat combined with the key to create the cipher text. The method of
combination is such that, it is hoped, an adversary could not determine the
meaning of the message without decrypting the message, for which he needs the
key.
Private-key methods are efficient and
difficult to break. However, one major drawback is that the key must be
exchanged between the sender and recipient beforehand, raising the issue of how
to protect the secrecy of the key.
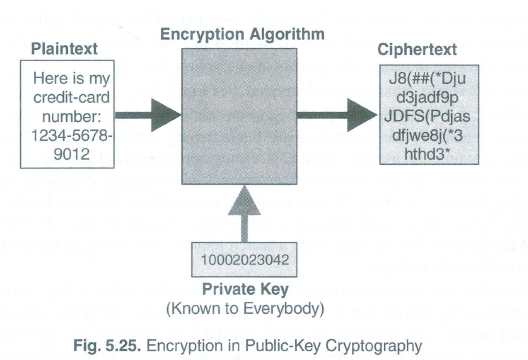
Public Key Cryptography
In public-key cryptography, two
separate keys are used to encrypt & decrypt data. The public key is shared
with the other person and the private key is known only to the person who
decrypts the data. So, the private key will remain a secret while the public
key will be known to both the parties.
Public-key cryptography depends upon
the notion of one-way functions: a one way function is a function that is easy
to apply, but extremely difficult to invert.
Digital Signature
A digital signature is an electronic
signature that can be used to authenticate the identity of the sender of a
message or the signer of a document, and possibly to ensure that the original
content of the message or document that has been sent is unchanged.
“Digital
signature is a computer data compilation of any symbol or series of symbols,
executed, adopted or authorized by an individual to be legally binded
equivalent to the individual’s handwritten signature”
v A digital signature authenticates
electronic documents in a similar manner a handwritten signature authenticates
printed documents.
v A digital signature is issued by a
Certification Authority (CA) and is signed with the CA’s private key.
v The recipient of a digitally signed
message can verify that the message originated from the person whose signature
is attached to the document and that the message has not been altered either
intentionally or accidentally since it was signed. Also the signer of a
document cannot later disown it by claiming that the signature was forged.
v When a message with a digital
signature is transmitted & received, the following parties are involved:-
Ø The signer who signs the document.
Ø The verifier who receives the signed
document & verifies the signature.
Ø The arbitrator who arbitrates any
disputes between the signer & the verifier if there is a disagreement on
the validity of the digital signature.
v A digital signature typically contains
the Owner’s public key, the Owner’s name, Expiration date of the public key,
the name of the issuer (the CA that issued the Digital ID), Serial no. of the
digital signature and the digital signature of the issuer.
v Digital signatures are based on a
combination of public key encryption and one way hash function that converts a
message of any length into a fixed length message digest known as hash
function. The value of hash function is unique for the hashed data. Any change
in the data, even deleting or altering a single character, results in a
different value. The content of the hash data cannot be deduced from hash which
is why it is called ‘one way’. The encrypted hash, along with other
information, such as hashing algorithm is known as digital signature.
E-Commerce Notes
Unit-2
Lecture-3
Virtual Private Network
Ø
A
Virtual private network (VPN) extends a private network across a public
network, such as the internet.
Ø It enables a computer to send and
receive data across shared or public networks as if it were directly connected
to the private network.
Ø This is done by establishing a
virtual point-to-point connection through the use of dedicated connections,
encryption or a combination of the two.
Ø VPN allows employees to securely
access their company’s intranet while travelling outside the office.
Ø Similarly, VPNs securely and cost
effectively connect geographically disparate offices of an organization,
creating one cohesive virtual network.
Ø
VPN
technology is also used by ordinary Internet users to connect to proxy servers
for the purpose of protecting one’s identity.
Types of VPN:
·
Remote
Access VPN
·
Site-to-Site
VPN
Ø Remote Access VPN:- Remote access VPNs allow employees to access their
company’s intranet from home or while travelling outside the office.
Ø Site-to-Site VPN:- Site-to-Site VPN allow employees in geographically
disparate offices to share on cohesive virtual network.
VPN systems may be classified by:-
·
The
protocols used to tunnel the traffic.
·
The
tunnel’s termination point location.
·
Whether
they offer site-to-site or remote access connectivity.
·
The
level of security provided.
VPN Architecture
There are two basic VPN architectural
choices:-
Ø Service provider independent VPN
Ø Service provider dependent VPN
·
Service provider independent VPN:- In a service provider independent
solution, a VPN enabled client(such as a desktop or laptop) initiates the
tunnel through the public network to the central site. To access the computer
network, the client first establishes a PPP (Point-to-Point protocol) session
to a local Internet Service Provider (ISP) for internet access. The client then
connects across the Internet to the central site and establishes a tunnel to
carry the data traffic. To the ISP the tunnel is simply data, and there is no
requirement for processing.
Advantage:
The advantage to the corporation is that it can use
any Point of Presence (POP) anywhere in the world, as long as it provides
Internet access. In addition, since the tunnel is initiated at the location of
the client, the client can travel with the same ease as carrying a laptop.
Disadvantage:
The disadvantage of this solution is that the client
must be VPN enabled. This could be prohibitively expensive to deploy for a
large no. of remote users.
·
Service provider dependent VPN:- With a service provider dependent
VPN model, the corporation enters into an agreement with a service provider
such as an ISP. The corporation user dials into a local POP with a PPP client,
and the tunnel session is initiated at the POP. The crucial difference is that
the client can be any PPP client.
Advantage
This arrangement can be combined with quality of
service agreements to guarantee a level of VPN performance, although few
service providers offers true guarantees today. Another advantage is that no
additional skills are required by the user to execute a tunnel to the company
LAN.
Disadvantage
Data security is critical because VPN encryption does
not occur until the POP, thus leaving the enterprise communication unprotected
between the remote PC and the POP.
VPN Security
v To prevent disclosure of private
information, VPNs typically allow only authenticated remote access and make use
of encryption techniques. VPN provides security by the use of tunneling
products and through security procedures such as encryption.
v The VPN security provides:
·
Confidentiality
·
Authentication
·
Integrity
v VPNs ensure privacy by providing a
private tunnel through the internet for remote access to the network. For full
VPN security, your VPN must be enhanced with a reliable user authentication
mechanism, protecting end points of the VPN.
v Username and password authentication
is not enough-this method is weak and highly susceptible to hacking, cracking,
key loggers and other attacks. It only takes one compromised password for your
organization to lose control over gains network access. Strong user authentication
with a VPN provides true secure remote access for today’s mobile workforce.
E-Commerce Notes
Unit-2
Lecture-4
Types of Security Attacks
v Passive Attack
v Active Attack
Ø Passive Attack: In Passive attack a network intruder
intercepts data travelling through the network. A passive attack monitors
unencrypted traffic. Passive attacks include traffic analysis, monitoring of
unprotected communications, capturing authentication information such as
passwords.
Types of Passive
Attacks:
a)
Wire Tapping or Telephone Tapping: Telephone tapping is the monitoring
of telephone and internet conversations by a third party. Passive wire tapping
monitors or records the traffic.
b)
Port Scanner: A port scan can be defined as an
attack that sends client requests to a range of server port addresses on a
host, with a goal of finding an active port and exploiting a known
vulnerability of that service.
c)
Idle Scan: The idle scan is a TCP port scan
method that consists of sending spoofed packets to a computer to find out what
services are available. This is accomplished by impersonating another computer
called a “zombie” and observing the behavior of the “zombie” system.
Ø Active Attack: In active attacks intruder initiates commands to disrupt
the network’s normal operation. In an active attack, the attacker tries to
bypass or break into secured systems. This can be done through viruses or
worms. Active attacks include attempts to break protection features to introduce
malicious code, and to steal or modify information.
Types of Active
Attacks
a)
Denial-of-service Attack (Dos): Denial of service attack is an
attempt to make a machine or network resources unavailable to its intended
users. It generally consists of efforts to temporarily or indefinitely
interrupt or suspend services of a host connected to the Internet. One common
method of attack involves saturating the target machine with external
communication requests, so much so that it cannot respond to legitimate traffic
or responds so quickly as to be rendered essentially unavailable. Such attacks
usually lead to a server overload.
b)
Spoofing attack: A spoofing attack is when a
malicious party impersonates another device or user on a network in order to
launch attacks against network hosts , steal data, spread malware or bypass
access controls.
c)
Man-in-the-middle attack: The man-in-the middle is a form of
active eves dropping in which the attacker makes independent connections with
the victims & relays messages between them, making them believe that they
are talking directly to each other over a private connection, while in fact the
entire conversation is controlled by the attacker. The attacker must be able to
intercept all messages going between the two victims & inject new ones.
d)
SQL injection: Sql injection is a code injection
technique, used to attack data driven applications, in which malicious SQL
statements are inserted into an entry field for execution.
Difference between Computer Virus and Computer Worm
Sno.
|
Computer
Virus
|
Computer
Worm
|
1.
|
It cannot be
controlled remotely.
|
It can be controlled remotely.
|
2.
|
It deletes,
modifies the files and also change the location of file.
|
It only monopolies the CPU & memory.
|
3.
|
It is slower
than worm
|
Worm is faster than virus.
|
4.
|
The virus is
the program code that attaches itself to application program and when
application program run it runs along with it.
|
The worm is code that replicate itself in order to
consume resources to bring it down.
|
E-Commerce Notes
Unit-2
Lecture-5
Intranet
Intranet Software enables an organization to securely share it's information
or operations with it's members. It enables the efficient use and more
importantly reuse of an organization's gathered business knowledge and
intelligence, which increases productivity and knowledge transfer in any
organization. Increasingly, extranets are also coming into use, where external
partners, customers can also interact with an organization. E.g. ERP software
that provides a centralized repository of information for massive amount of transaction
and details generated daily.
The cost of converting an existing client-server network to
an intranet is relatively low, especially when a company is already using the
Internet.
Applications of Intranet:
The most popular intranet application is obviously:
1.
Inter-office e-mail, this capability allows
the employees of a company to communicate with each other swiftly and easily.
If the intranet has access to the Internet, e-mail can be accessed through the
Internet connection. If the intranet is running without the Internet, special
e-mail software packages can be bought and installed so that employees can take
advantage of its many benefits.
2.
An
intranet has many other different applications that can be utilized by a
company. These include the Web publishing of corporate documents, Web forms,
and Web-to-database links that allow users to access information.
3.
Newsletters,
information on benefits, job listings and classifieds, libraries, stock quotes,
maps, historical data, catalogs, price lists, information on competitors'
products, and customer service data are just a few examples of these types of
applications.
In
addition, there are several other main applications that is very popular in the
intranet format:-
1.
Document publication applications
The first application that
always comes to mind for intranets in and of themselves is the publication and
distribution of documents. This application allows for paperless publication of
any business information that is needed for internal employees or external customers
or suppliers. Any type of document may be published on an intranet: policy and
procedure manuals, employee benefits, software user guides, online help,
training manuals, vacancy announcements--the list goes on to include any
company documentation.
2.
Electronic resources applications
In the past it has not been
easy to share electronic resources across network nodes. Employees have had
problems sharing information for various reasons including software version
inaccuracies and incompatibilities. Intranets provide the means to catalog resources
online for easy deployment across the network to any authorized user with the
click of a mouse. Software applications, templates, and tools are easily
downloaded to any machine on the network.
3.
Interactive communication applications
Two-way communications and
collaboration on projects, papers, and topics of interest become easy across
the intranet. Types of communications that are enhanced and facilitated include
e-mail, group document review, and use of groupware for developing new
products.
4.
Support for Internet applications
Even though organizational
full-service intranets are the next step in enterprise-wide computing and have
enough value to make them desirable simply for the organizational benefits they
bring, they are also necessary for supporting any Internet applications that
are built.
The transactional processes and trading of information that will be done by all but the most elementary Web applications will require an infrastructure to store, move, and make use of the information that is traded. The infrastructure to accomplish those tasks is the organizational intranet.
The transactional processes and trading of information that will be done by all but the most elementary Web applications will require an infrastructure to store, move, and make use of the information that is traded. The infrastructure to accomplish those tasks is the organizational intranet.
Generic Functions of Intranet:
Major generic functions that intranet
can provide are:
·
Corporate/ department/ individual WebPages: Access the web- pages of corporate, departments and
individual.
·
Database access:
Web- based database.
·
Search engines and directories: It assists the keyword- based search.
·
Interactive communication: chatting, audio and videoconference.
·
Document distribution and workflow: web- based download and routing of documents.
·
Groupware:
E-mail and bulletin board.
·
Telephony:
intranet is the perfect conduit for computer-based telephony.
·
Extranet:
linking geographically dispersed branches, customers and suppliers to
authorized sections of intranets creates happiest customers, more efficient
suppliers, and reduced staff cost.
Considerations in Intranet Deployment:
1.
Collections of
web links
2.
Company news and
department newsletters
3.
Organization
charts
4.
Manuals, documentation,
policies
5.
Basic
collaboration tools (groupware)
6.
Directory
services (gateway to phone and other staff contact info)
7.
Human resources
information
8.
Threaded
discussions on current company topics/issues
9.
Web–based email
access
10.
Web–based
discussion list management and participation
11.
Access to company
databases — sales, inventory, pricing
12.
Calendaring
(company–wide events calendar)
13.
Scheduling
(meetings, personal scheduling)
14.
Document
management
15.
Search engine of
company documents
16.
Employee time
logging
17.
Employee expense
reporting
18.
Forms to help
automate other business processes – work
orders, job descriptions, mileage, maintenance requests, etc.
Intranet Application Case Studies:
Now, let us investigate some typical
application case in depth, including their return on investment (ROI).
Intranet Case studies with ROI Analysis:
The need for accountability and for
clear measures of success is increasingly demanded for all corporate
expenditures, including intranets. If you are responsible for an intranet, you
need to know how build a business case and develop a return on investment (ROI)
strategy.
Intranet ROI
Intranets and corporate portals are expensive
endeavors. Despite the expense, many organizations understand the implicit
and/or explicit value. Intranets are widely valued for:
- Streamlining
business processes and driving operational efficiencies
- Significantly
reducing cost of internal business functions
- Enhancing
communications and collaboration between employees, managers, suppliers
and partners
As with any critical business system, an
intranet or portal must be delivering measurable performance and remain
accountable to the investment. If the site’s value is not being measured, then
it risks failing the needs and demands of employees and management.
When asked how executives determine whether an
intranet or portal is delivering value, they typically point to reducing costs
and improving productivity.
Of course, IT budgets are increasingly tied to
company-wide business and strategic initiatives. The cost justification for any
expenditure, including IT must have a clear bottom line that answers the
question, “What’s the payback?”
In recent years, business challenges and
subsequent solutions/applications have been the driving force behind intranet
investments. They will continue to play this role in the future.
Executives will make investments in intranets
and portals (see defining in the adjacent glossary) if such investments spur
growth, cut the cost of operations, and/or help enhance the customer experience
(retaining and building the customer base).
The challenging economic climate of the past
few years means that more and more organizations will allocate dollars to IT
systems and applications that can demonstrate a measured solution and ROI to a
business problem or provide enhanced service and growth.
Short
Intranet Application Cases
Prescient Digital Media is a veteran web and
intranet consulting firm. It provides strategic Internet and intranet
consulting, planning and design services to many Fortune 500 and big brand
clients, as well as small and medium-sized leaders. It treat each client as
unique; It listen to their needs, goals
and challenges; understand a client's requirements and potential; and deliver
highly effective and innovative website and intranet plans, designs and
solutions.
ROI Study Of the respondents to the
Prescient Digital Media ROI survey that undertake ‘rough estimates’
of their organization’s intranet, answers varied from $0 to $20M. The
average annual ROI of respondent intranets fell just shy of $1
million ($979,775.58).
While less than 20% of organizations have
measured specific benefits, a majority of organizations have at the very least
made a ‘rough estimate’ or guess of the value of their ROI. While only a
handful of technology companies measured intranet ROI three years ago, there
are encouraging signs of change. A recent study, conducted by Prescient Digital
Media Ltd., finds that 6% of organizations undertake ongoing, specific
measurement of the ROI of their intranet. Occasional measurement is undertaken
by 26% of the respondent organizations.
While extensive ROI measurement has not yet
become mandatory at a majority of organizations with intranets, ROI is a
priority in 76% of the survey respondents. Rather than attempt to measure the
intranet or portal’s entire value, those companies that are successfully
gauging value are measuring specific benefits. This paper lists intranet
benefits in 10 key categories – including hard costs, increased revenue, etc. –
with two supporting categories: content management and procurement.
The precision, scope of work and execution
required to build and maintain a successful intranet or portal is massive –
from governance to content management, and from technology to business
processes. At the heart of a successful intranet is the strength of the
underlying plan. Failure to develop an integrated plan that accounts for an
organization’s structure, stakeholder, and user requirements will almost
certainly ensure failure and, with it, a loss of significant time, money and
jobs.
Finally, while appraising the ROI of an
intranet or portal is critical for most executives, there exists a great deal
of untapped, intangible value that is perhaps even more critical than the
measured dollars and cents. When properly deployed, intranets improve
communication and collaboration and improve employee satisfaction, which in
turn can improve productivity. All benefits are clearly important to any
organization, but not always a measurable ROI.
Share
Knowledge Among Corporate Employee
Intranets offer several facilities that aid
knowledge sharing:
Easy-to-access
and use: The use
of World Wide Web (WWW) browsers give a low cost and easy-to-use interface to
information and applications
Universal
access to information:
Information can be kept on any 'server' on the network, and can be accessed
from anywhere within the Intranet.
Person-to-person
interaction:
Intranets simplify interaction between people in different locations, through
electronic mail, and computer conferencing
Informal
networks:
Publishing information and making contact is quick and informal on an Intranet.
Scalable
networks: As
organizations restructure, it is easy to add or remove servers to the overall
network.
Access
to external information and knowledge:
Intranets usually have gateways to the external Internet, which give access to
a rapidly growing global information resource
E-Commerce Notes
Unit-2
Lecture-6
Firewall
v Firewall is software or hardware
based network security system that controls the incoming and outgoing network
traffic by analyzing the data packets and determining whether they should be
allowed through or not, based on a rule set.
v A firewall establishes a human
barrier between a trusted, secure internal network & another network that
is not assumed to be secure and trusted.
v Many personal computer operating
systems include software-based firewalls to protect against threats from the
public Internet. Many routers that pass data between networks contain firewall
components and conversely many firewalls can perform basic routing functions.
Types of Firewall
Ø Network Layer or Packet Filters
Firewall
Ø Application Layer Firewall
Ø Proxy Firewall
Ø Unified Threat Management(UTM)
Network Layer or Packet Filters Firewalls
Network layer firewalls, also called
packet filters, operate at a relatively low level of the TCP/IP protocol stack,
not allowing packets to pass through the firewall unless they match the
established rule set.
A simple router is the traditional
network layer firewall, since it is not able to make particularly complicated
decisions about what a packet is actually taking to or where it actually came
from. Modern network layer firewalls have become increasingly more sophisticated
& now maintain internal information about the state of connections passing
through them at any time.
Application Layer Firewalls
Application layer firewalls work on
the application level of the TCP/IP stack, and may intercept all packets traveling
to or from an application. They block other packets (usually dropping them
without acknowledgement to the sender).
On inspecting all packets for proper
content, firewalls can restrict or prevent outright the spread of networked
computer worms and Trojans.
Proxy Firewalls
Proxy firewalls offer more security
than other types of firewalls. Unlike application layer firewalls which allow
or block network packets from passing to and from a protected network, traffic
does not flow through proxy. Instead computers establish a connection to the
proxy which serves as an intermediary and initiate a network connection on
behalf of the request. This prevents direct connections between systems on
either side of the firewall and makes it harder for an attacker to discover
where the network is, because they will never receive packets created directly
by their target system.
Unified Threat Management
A product category called unified
threat management (UTM) has emerged. These device promise integration,
convenience & protection from pretty much every threat out there and are
especially valuable to small & medium-sized businesses.
Unified Threat Management is a
firewall appliance that not only guards against intrusion but performs content
filtering, spam filtering, intrusion detection & anti-virus duties
traditionally handled by multiple systems. These devices are assigned to combat
all levels of malicious activity on the computer network.
E-Commerce Notes
Unit-2
Lecture-7
Electronic Payment Systems
Electronic Payment is a financial
exchange that takes place online between buyers and sellers. The content of
this exchange is usually some form of digital financial instrument (such as encrypted
credit card numbers, electronic cheques or digital cash) that is backed by a
bank or an intermediary, or by a legal tender.
The
various factors that have lead the financial institutions to make use of
electronic payments are:
1. Decreasing
technology cost:
The technology used in the networks is decreasing day
by day, which is evident from the fact that computers are now dirt-cheap and
Internet is becoming free almost everywhere in the world.
2. Reduced
operational and processing cost:
Due to reduced technology cost the processing cost of
various commerce activities becomes very less. A very simple reason to prove
this is the fact that in electronic transactions we save both paper and time.
3. Increasing
online commerce:
The above two factors have lead many institutions
to go online and many others are following them.
There are
also many problems with the traditional payment systems that are leading to its
fade out. Some of them are enumerated below:
1. Lack of
Convenience:
Traditional payment systems require the
consumer to either send paper cheques by snail-mail or require him/her to
physically come over and sign papers before performing a transaction. This may
lead to annoying circumstances sometimes.
2. Lack of
Security:
This is because the consumer has to send
all confidential data on a paper, which is not encrypted, that too by post
where it may be read by anyone.
3. Lack of
Coverage:
When we talk in terms of current
businesses, they span many countries or states. These business houses need
faster transactions everywhere. This is not possible without the bank having
branch near all of the company’s offices. This statement is self-explanatory.
4. Lack of
Eligibility:
Not all potential buyers may have a bank
account.
5. Lack of
support for micro-transactions:
Many transactions done on the Internet
are of very low cost though they involve data flow between two entities in two
countries. The same if done on paper may not be feasible at all.
Types of
Electronic Payment System
1.
Electronic Tokens
An electronic token is a digital analog of various
forms of payment backed by a bank or financial institution. There are two types
of tokens:
·
Real Time: (or Pre-paid tokens) - These are exchanged between buyer and seller, their
users pre-pay for tokens that serve as currency. Transactions are settled with
the exchange of these tokens. Examples of these are DigiCash, Debit Cards,
Electronic purse etc.
·
Post Paid Tokens – are used with fund transfer instructions between the buyer and
seller. Examples – Electronic cheques, Credit cards etc.
2.
Credit Cards
·
A
credit card is a small plastic card issued to users as a system of payment.
·
It
allows its holders to buy goods & services based on the holder’s promise to
pay for these goods and services.
·
Essentially
a credit card allows you to:-
Ø Purchase products or services
whenever and wherever you want, without ready cash and paying for them at a
later date.
Ø Have an option of paying only a part
of the total expenses. The balance amount can be carried forward, with an
interest charged.
Ø Enjoying a revolving credit limit
without any charges for a limited period (mostly 20 to 50 days).
Types of Credit Cards
1.
Standard Credit Card: The most common type of credit card
allows you to have a revolving balance up to a certain credit limit. These
credit cards have a minimum payment that must be paid by a certain due date to
avoid late payments.
2.
Premium Credit Cards: These cards offer incentives and
benefits beyond that of a regular credit card. Examples of premium credit cards
are gold and platinum cards that offer cash back, reward points, travel
upgrades and other rewards to cardholders.
3.
Charge Cards: Charge cards do not have a credit
limit. The balance on a charge card must be paid in full at the end of each
month. Charge cards do not have a minimum payment since the balance is to be
paid in full. Late payments are subject to a fee, charge restrictions, or card
cancellation depending on your card agreement.
4.
Limited Purpose Card: Limited purpose credit cards can
only be used at specific locations. Limited purpose cards are used like credit
cards with a minimum payment & finance charge. Store credit cards & gas
credit cards are examples of limited purpose credit cards.
5.
Secured Credit Card: Secured credit cards are an option
for those without a credit history or those with blemished credit. Secured
cards require a security deposit to be placed on the card. The credit limit on
a secured credit card is equal to the amount of the deposit made.
6.
Prepaid Credit Card: Prepaid credit cards require the
cardholder to load money onto the card before the card can be used. The credit
limit does not renew until more money is loaded onto the card. Prepaid cards
are similar to debit cards, but are not tied to a checking account.
7.
Business credit card: Business credit cards are designed
specifically for business use. They provide owners with an easy method of
keeping business & personal transactions separate.
The Players
Before exploring the
process of using credit card online, let’s identify the players in the credit
card system. They are:
The card holder: a consumer or a corporate purchaser who uses credit cards to pay
merchant.
The merchant: the entity that accept credit cards and offers goods or services in
exchange for payments.
The card issuer: a financial institution (usually a bank) that establishes accounts
for cardholders and issues credit cards.
The acquirer: a financial institution (usually a bank) that establishes accounts
for merchants and acquires the vouchers of authorized sales slip.
The card brand: bank card associations of issuers acquires ( like Visa and
MasterCard) which are created to protect and advertise the card brand,
establish and enforce rules for use and acceptance of their bank cards and
provide networks to connect the involved financial institutions. The brand
authorizes the credit- based transaction and guarantees the payment to
merchants. Sometimes the issuing bank performs the business of the brand.
The process of using credit card:
1.
Issue a
credit card to a potential card holder.
2.
The
cardholder shows the card to a merchant whenever he/she needs to pay for a
product or services.
3.
The merchant
then asks for approval from the brand company, and the transaction is paid by
the credit. The merchant keeps a sales slip.
4.
The merchant
sells the slip to the acquiring bank and pays a fee for the service. This is
called the capturing process.
6.
The amount is transferred
from issuer to brand. The same amount is deducted from the cardholder’s account
in the issuing bank.
Advantages of Credit Cards:
Ø They allow you to make purchases on
credit without carrying around a lot of cash.
Ø They allow convenient remote
purchasing ordering/shopping online or by phone.
Ø They allow you to pay for large
purchases in small, monthly installments.
Ø Many cards offer additional benefits
such as additional insurance cover on purchases, cash back, air miles &
discounts on holidays.
Ø
Under
certain circumstances, they allow you to withhold payment for merchandise which
proves defective.
Disadvantages of Credit Cards:
Ø
You
may become an impulsive buyer and tend to overspend because of the ease of
using credit cards. Cards can encourage the purchasing of goods & services
you cannot really afford.
Ø Lost or stolen cards may result in
some unwanted expense & inconvenience.
Ø The use of large no. of credit cards
can get you even further into debt.
Ø
Using
a credit card especially remotely introduces an element of risk as the card
details may fall into the wrong hands resulting in fraudulent purchases on the
cards. Fraudulent or unauthorized charges may take months to dispute,
investigate and resolve.
3.
Smart Cards
Ø A smart card is a plastic card about
the size of a credit card, with an embedded microchip that can be loaded with
data.
Ø Smart cards are made of plastics generally
polyvinyl chloride.
Ø Smart cards can provide
identification, authentication, data storage & application processing.
Ø A smart card contains more
information than a magnetic strip card and it can be programmed for different
applications.
Ø Smart cards within the next five
years will be the industry standard in debit and credit cards. As the major
high street banks and finance houses are now investing in the changeover to
smart card technology.
Ø You may use a smart card to:-
·
Establish
your identity when logging on to an Internet access provider or to an online
bank.
·
Pay
for parking at parking meters or to get on subways, trains or buses.
·
Give
hospitals or doctors personal data without filling out a form.
·
Make
small purchases at electronic stores on the web.
Advantages of Smart Cards:
§ Greater Reliability
§ Storage Capacity is increased up to
100 times.
§ Smart cards are multifunctional.
§ The anticipated working life of a
smart card is ten years compared to that of a magnetic strip card.
4. Electronic Cheques
The electronic cheques are modeled on paper cheques,
except that they are initialted electronically.
They use digital signatures for signing and endorsing
and require the use of digital certificates to authenticate the payer, the
payer’s bank and bank account.
Electronic checks allow merchants to convert paper
check payments made by customers to electronic payments that are processed
through the Automated Clearing House
(ACH).
How Electronic
Cheques work:
When you receive a paper cheque payment from your customer
, you will run the cheque through an electronic scanner system supplied by your
merchant service provider. This virtual terminal captures the customer’s
banking information and payment amount written on the cheque. The information
is transferred electronically via the Federal Reserve Bank’s ACH Network, which
takes the funds from your customer’s account & deposits them to yours.
Once the cheque has been processed & approved, the
virtual terminal will instantly print a receipt for the customer to sign &
keep.
Benefits of
Electronic Cheques:
·
Secure
and quick settlement of financial obligations.
·
Fast
cheque processing
·
Very
low transaction cost.
5.
Electronic or Digital Cash
A system that allows a person to pay for
goods or services by transmitting a number from one computer to another.
Like the serial numbers on real dollar
bills, the digital cash numbers are unique. Each one is issued by a bank &
represents a specified sum of money.
Digital Cash combines computerized
convenience with security and privacy that improve upon paper cash. Cash is
still the dominant form of payment as: The consumer still mistrusts the banks.
The non-cash transactions are inefficiently cleared. In addition, due to
negative real interests rates on bank deposits.
Digital cash is based on cryptographic
systems called "Digital Signatures" similar to the signatures used by
banks on paper cheques to authenticate a customer.
Some qualities
of cash:
a. Cash is a legal tender i.e. payee is obligatory to
take it.
b. It is negotiable i.e. can be given or traded to
someone else.
c.
It is a bearer
instrument i.e. possession is proof of ownership.
d. It can be held & used by anyone, even those
without a bank certificate.
e. It places no risk on part of acceptor.
The following are the limitations of
Debit and Credit Cards:
i.
They are
identification cards owned by the issuer & restricted to one user i.e.
cannot be given away.
ii.
They are not
legal tender
iii.
Their usage
requires an account relationship and authorization system.
Properties
of Digital Cash
o Must have a monetary value: It must be backed by cash (currency), bank authorized
credit or a bank certified cashier’s check.
o Must be interoperable or exchangeable: as payment for other digital cash, paper cash, goods
or services, lines of credit, bank notes or obligations, electronic benefit
transfers and the like.
o Must be storable and retrievable: Cash could be stored on a remote computer’s memory,
in smart cards, or on other easily transported standard or special purpose
devices. Remote storage or retrieval would allow users to exchange digital cash
from home or office or while traveling.
6.
Debit Cards
A debit card is a plastic payment card that provides
the cardholder electronic access to his or her bank account at a financial
institution.
Types of Debit Card Systems:
·
Online
Debit or Pin Debit
·
Offline
Debit or Signature Debit
Online Debit System: Online debit system requires
electronic authorization of every transaction and the debits are reflected in
the user’s account immediately. The transaction may be secured with the
personal identification number (PIN) authentication system.
Offline Debit System: Offline debit system may be subject
to a daily limit. Transactions conducted with offline debit cards, require 2-3
days to be reflected on user’s account balances.
Advantages of Debit Cards:
·
There
is no need to carry cash
·
It
is quick and less complicated than using a cheque.
·
It
can be used for withdrawals of cash.
·
It
can be issued to any individual without assessing credit worthiness.
·
Its
holders can have a record of the transactions in his bank statement which will
enable him to plan and control the expenditure.
7.
Electronic Wallet/Purse
A digital/electronic wallet refers to
an electronic device that allows an individual to make electronic commerce transactions. This can include
purchasing items on-line with a computer or using a smartphone to purchase
something at a store.
Increasingly, digital wallets are
being made not just for basic financial transactions but to also authenticate
the holder's credentials. For example, a digital-wallet could potentially
verify the age of the buyer to the store while purchasing alcohol.
It is useful to approach the term
"digital wallet" not as a singular technology but as three major
parts: the system (the electronic infrastructure) and the application (the
software that operates on top) and the device (the individual portion).
An individual’s bank account can also
be linked to the digital wallet. They might also have their driver’s license,
health card, loyalty card(s) and other ID documents stored on the phone. The
credentials can be passed to a merchant’s terminal wirelessly via near field
communication (NFC).
Certain sources are speculating that these Smartphone “digital wallets” will
eventually replace physical wallets.
A digital wallet has both a software and information
component. The software provides security and encryption for the personal
information and for the actual transaction.
Typically, digital wallets are stored on the client side and
are easily self-maintained and fully compatible with most e-commerce Web sites. A server-side digital wallet, also known as a
thin wallet, is one that an organization creates for and about you and
maintains on its servers. Server-side digital wallets are
gaining popularity among major retailers due to the security, efficiency, and
added utility it provides to the end-user, which increases their enjoyment of
their overall purchase.
Advantages of Electronic Payment System
·
Decreasing Technology cost
The technology used in the networks
is decreasing day by day, which is evident from the fact that computers are now
dirt cheap and Internet is becoming free almost everywhere in the world.
·
Reduced operational and processing
cost
Due to reduced technology cost the
processing cost of various commerce activities become very less. A very simple
reason to prove this is the fact that in electronic transactions we save both
paper and time.
·
Increasing online commerce:
The above two factors have lead many
institutions to go online and many others are following them.
Drawbacks
or Risks in Electronic Payment System
Electronic payment is a popular method of making
payments globally. It involves sending money from bank to bank instantly --
regardless of the distance involved. Such payment systems use Internet
technology, where information is relayed through networked computers from one
bank to another. Electronic payment systems are popular because of their
convenience. However, they also may pose serious risks to consumers and
financial institutions.
·
Tax Evasion
Businesses are required by law to
provide records of their financial transactions to the government so that their
tax compliance can be verified. Electronic payment however can frustrate the
efforts of tax collection. Unless a business discloses the various electronic
payments it has made or received over the tax period, the government may not
know the truth, which could cause tax evasion.
·
Fraud
Electronic payment systems are prone to fraud. The
payment is done usually after keying in a password and sometimes answering
security questions. There is no way of verifying the true identity of the maker
of the transaction. As long as the password and security questions are correct,
the system assumes you are the right person. If this information falls into the
possession of fraudsters, then they can defraud you of your money.
·
Impulse Buying
Electronic payment systems encourage impulse buying,
especially online. You are likely to make a decision to purchase an item you
find on sale online, even though you had not planned to buy it, just because it
will cost you just a click to buy it through your credit card. Impulse buying
leads to disorganized budgets and is one of the disadvantages of electronic
payment systems.
·
Payment Conflict
Payment conflicts often arise because the payments are
not done manually but by an automated system that can cause errors. This is
especially common when payment is done on a regular basis to many recipients.
If you do not check your pay slip at the end of every pay period, for instance,
then you might end up with a conflict due to these technical glitches, or
anomalies.
E-Commerce Notes
Unit-2
Lecture-8
Extranet
·
Extranet
is an extended intranet that connects multiple intranets through a secured
tunneling internet.
·
Extranets
act as a link to select individuals outside the company by allowing them access
to the information stored inside the intranet.
·
Internet
protocols are typically utilized by extranets so as to provide browser
navigation even though the network is situated on a private server. A username
and password system can be configured to sectors of the content so as to
prevent users from accessing information they have no authorization for.
·
Extranets
combine the privacy and security of intranets with the global reach of the
internet, granting access to outside business partners, suppliers, and costumers
to a controlled portion of the enterprise network. Extranets are becoming the
major platforms for B2B EC replacing or supplementing EDI. They provide
flexibility serving internal and external users.
Extranets
generally have the following features:
Ø The use of Internet technologies and standards. These include the standardized techniques for
transmitting and sharing information and the methods for encrypting and storing
information, otherwise known as the Internet Protocol, or IP.
Ø The use of Web browsers. Users access extranet information using a web
browser like Microsoft Internet Explorer, Netscape Navigator or, more recently,
Mozilla’s Firefox. Browser software uses relatively small amounts of memory and
resources on a computer. The great thing about browsers is that an application
written for a browser can be read on almost any computer without regard to
operating system or manufacturer. That makes an application developed for a
browser a snap to deploy. A browser on a user’s machine is all the software he
or she needs to take full advantage of the extranet application. No messy and
confounding installation disks; fewer clogged hard drives.
Ø Security. By
their very nature, Extranets are embroiled in concerns about security. To
protect the privacy of the information that is being transmitted, most
Extranets use either secure communication lines or proven security and
encryption technologies that have been developed for the Internet.
Ø Central Server/Repository. Extranets usually have a central server where documents
or data reside. Members can access this information from any computer that has
Internet access.
While these are the broad attributes shared by
most Extranets, Extranets vary dramatically in their design and implementation.
They can be employed in a wide variety of environments and for very different
purposes, like:
- Sharing
case information
- Sharing
of case-related documents—many Extranets contain document repositories
that can be searched and viewed by both lawyer and client on-line
- Calendaring—key
dates and scheduling of hearings and trials can be shared on-line
- Providing
firm contact information
- Acting as a “work flow engine” for various
suppliers
- Providing access to firm resources remotely
- Sharing time and expense information.
Extranet applications Case
An extranet application is a software data application that
provides limited access to your company's internal data by outside users such
as customers and suppliers. The limited access typically includes the ability
to order products and services, check order status, request customer service
and much more.
A properly developed extranet application provides the supply chain connection needed with customers and suppliers to dramatically lessen routine and time consuming communications. Doing so frees up resources to concentrate on customer service and expansion as opposed to administrative office tasks such as data entry.
Just as intranets provide increased internal collaboration, extranets provide increased efficiencies between your company and its customers and/or suppliers. Developing and implementing an extranet application can provide you the competitive edge to stay ahead of the competition in the eyes of your customers and a better ability to negotiate prices with your suppliers.
A properly developed extranet application provides the supply chain connection needed with customers and suppliers to dramatically lessen routine and time consuming communications. Doing so frees up resources to concentrate on customer service and expansion as opposed to administrative office tasks such as data entry.
Just as intranets provide increased internal collaboration, extranets provide increased efficiencies between your company and its customers and/or suppliers. Developing and implementing an extranet application can provide you the competitive edge to stay ahead of the competition in the eyes of your customers and a better ability to negotiate prices with your suppliers.
Potential of Extranet Market
Internets are included in extranets, the forecasted potential
of extranets is frequently combined with that of the intranets. According to a
study by Gartner Group, Extranets are expected to be a platform of choice of
more than 80 % of B2B EC. This increasing acceptance is expected to surpass B2C
EC which is also expected to be conducted across intranets, by about 40
percent. Most of the B2C EC traffic will be done on the regular internet.
However many companies, such as FedEx, will allow costumer to enter their
intranets.
Planning Extranet
If you are considering introducing an intranet
or extranet into your business, you should ensure that it is flexible enough to
meet not only your immediate requirements, but also your needs as your business
grows. Make sure your objectives are clear. Will you restrict access to your
site, or will you allow all of your customers to use it? Do you want to promote
flexible working in your business by catering for your remote workforce? How
will you measure the success of your investment?
Identify the information that will need to be
made available in order to meet your objectives:
- What
kind of company information do you need on your intranet? For example,
company policies, news, forms and corporate branding.
- Do
you need to make all of your production and sales information available to
your partners via your extranet, or will discrete sub-sections be
sufficient?
- Web
server hardware and software. The size of the server will depend on the
number of potential users and whether or not you will need a lot of
bandwidth to support audiovisual content, eg video feeds.
- Computers
connected via a local area network - a closed, private network.
- Firewall
software and hardware, which will prevent unauthorized access from outside
your organization.
- A
content management system to add and update intranet content.
This might be a good arrangement if your
business is just starting up - you can develop your own intranet once your
business has grown and you have more funds available. Once you have your
intranet up and running, you can create your extranet by giving partners access
to the necessary company data via a log-in page. Identify the support costs
that will be required to run the site on a day-to-day basis. Will you require
technical support - if so, at what level? You should also consider how the
content will be managed. Remember that security is paramount, since any
security incident will directly affect not only you but also your key business
partners. You should establish what levels of security are provided when
choosing a technology solution.
Advantages/Benefits of Extranet
Ease of set-up, use
and maintenance: Extranets should be simple to set-up, use and
maintain. The time it takes to develop a complete and functioning extranet with
a robust Web-standard software solution amounts to days or weeks, rather than
months or years with proprietary networks solutions. Modifications can also be
implemented with little or no interruption to the extranet’s activities.
Scalability: Extranets
require the flexibility to grow to include additional users or organizations,
or to expand to a new hardware server array without compromising the system's
usability or integrity. Solutions written using non-industry standard format or
proprietary architectures can significantly restrict an extranet's ability to
scale to include new users, applications, servers or other components. Extranet
solutions eliminate the lock-in strategies used by software vendors and allow
for greater extensibility of the extranet to meet the growing and changing
demands of the on-line user community.
Versatility: An extranet
should serve fundamental business activities such as document exchange,
collaborative discussion groups, on-line submission forms, database queries,
etc. yet have the ability to be customized to satisfy a particular business
purpose. For example, companies transferring text or document files have
different requirements than those that transfer movies, video clips, other
multimedia files to be viewed on-line. Some organizations may wish to sell
directly on-line through the extranet and others may wish to only automate the
back office operations. Regardless of the business objective, extranets require
versatility to accommodate a dynamic company's changing mission, goals and
objectives.
Security: Security is
perhaps the single most important characteristic possessed by an extranet that
serves multi-organizational interests. Ensuring that all participant and
contributor content is protected within a secure and accountable framework
provides the basis for system usability and dependability. Although no system
is ever 100% secure, recent advances in security technology provide extranets
with security that exceeds industry standards and protects on-line information
and intellectual property.
Business Models of Extranet Applications
The extranet represents the bridge between the public
Internet and the private corporate intranet. The extranet connects multiple and
diverse organizations on-line, enabling strategic communities of stakeholders
with common interests (communities of interests) to form a tight business
relationship and a strong communication bond, in order to achieve
commerce-oriented objectives. The extranet defines and supports this extended
business enterprise including partners, suppliers and distributors,
contractors, customers and others that operate outside the physical walls of an
organization but are nonetheless critical to the success of business
operations. With the Internet providing for public outreach or communication,
and intranets serving internal business interests, extranets serve the
business-critical domain between these extremes where the majority of business
activity occurs.
Fig: Business Model for
Extranet
The unification of robust enabling technologies and
ubiquitous access through the Web is resulting in unique and interesting market
dynamics that are changing the way many companies are doing business.
Interactive communities are beginning to emerge that exist
solely in cyberspace, where information travels faster, more cost effectively,
and with greater accuracy when compared to other forms of communication and
information exchange. These interactive communities are the driving and
sustaining force behind the extranet concept, and their insatiable collective
need to access content when, where, and how they want to see it will continue
to push the limits of what is technologically possible. Extranet solutions
built to engage and support these interactive communities are designed to
emphasize and foster customer relationships. As successful businesses know, the
cost of obtaining a new customer far outweighs the cost of maintaining a
current one.
With commerce-enabled extranets, companies are now able to
establish and maintain one-to-one relationships with each of their customers,
members, staff or others at very low cost through the Web, offering a
customized and individualized experience that can be dynamically generated or
modified based upon a user's privileges, preferences, or usage patterns.
Information entered by the user (registration form, on-line surveys, etc.) can
be compiled with statistics and other information that is captured
automatically by the system (searches performed, products purchased, time spent
in each site area, etc.) to provide the company a complete picture for each and
every visitor of the system. This comprehensive user profile offers
unprecedented opportunities to present relevant information, advertising,
product and service offerings and other content to a qualified, targeted
interactive user community on a one-to-one basis.
Fig: Interaction of
consumer community and Organization
Managerial
Issues
Management is no longer worries about
whether or not to adopt the intranet/ extranet but is concerned about how to
utilize them successfully for business.
Intranets/ Extranets are already two facts of life in many large
corporations. Thus management needs to review it’s own company’s position in
dealing with a verity of issues in installing the internet/ extranet. The
following are the guidelines for managerial issues:
1.
Find the business opportunities by
utilizing the intranet and extranet: for example, consider connecting the customer, suppliers
and internal branches that are geographically dispersed.
2.
Analyze whether the connectivity
requirement suits the intranet and extranet: it is mainly dependent upon whether the network is
composed of one LAN or multiple LANs. The former is suitable for internet and
the latter for extranet. Individual’s remote access should also be considered.
3.
Plan the most secure economical
choice for implementation: consult the technical persons and outside the company for
implementation. Review the current proprietary or leased network and determine
if it can be replaced by intranet and extranet. It may reduce costs and widen
connectivity for the customers and suppliers.
4.
Select the best outsourcers for
implementation:
compare the outsourcers who can implement the internet/ extranet. The extranet
solution providers can cultivate new opportunities in this big market.
5.
Selling the intranet: corporate intranet can serve as a
wonderful pool, where employees can do many things ranging from taking classes
to updating benefit plans. Too often employees are not using the intranet to
its fullest capacity. Businesses are exploring innovative ways to market their
intranet to their employees. For example some companied are making presentation
to employees, other give prizes, yet other created an “Intranet Day”.

















great post about e-commerce get the best E-commerce development noida
ReplyDeleteGreat post.
ReplyDeletehttp://www.folkd.com/user/RaghibFadi
Great post.
ReplyDeletehttps://www.question2answer.org/qa/user/AdliMajid
Great post.
ReplyDeletehttps://archive.org/details/@michaelthompson
Great post.
ReplyDeletehttps://wiseintro.co/virohaa
Great post.
ReplyDeletehttps://forum.freeadvice.com/members/steven-s-wendt.706452/#about
Great post.
ReplyDeletehttps://www.diyaudio.com/forums/members/blakebankston.html
Like the written by hand signature, which approves physical reports, electronic records can be approved by marking them utilizing an advanced mark. Vakilsearch site to get Class 3 digital signature
ReplyDeleteGreat article! Thanks for sharing an informative blog with us. I learn many new things from your article. I really like your post, It is very helpful for us. Please keep sharing these types of articles.
ReplyDeleteFantasy Sports App Development
Thanks for the information, click here to class 2 digital signature online
ReplyDeleteScale up your business with the CreditQ 2.0. Join CreditQ and progress towards your goal with the Business Credit Management services
ReplyDeleteThanks for sharing this post with us.Wikivela
ReplyDeleteUnit 2, Lecture 1 on e-commerce notes provides valuable insights. It covers fundamental concepts crucial for understanding the digital marketplace. Why Can't Support From transaction security to customer experience.
ReplyDelete